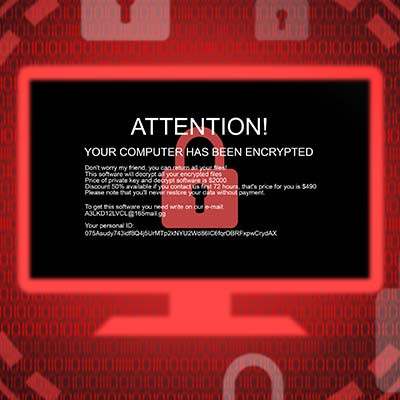
The cloud is far and away one of the most beneficial technologies that a modern business has at its disposal. Unfortunately, the same can be said for modern cybercriminals. The cloud has given cybercriminals new opportunities that are important to acknowledge—as well, of course, to protect your business against.
Request a Consultation
Flexnet Networks LLC strives to provide the best comprehensive IT, Computer, and Networking services to small businesses. We can handle all of your organization's technology challenges.
Contact UsContact Us
Learn more about what Flexnet Networks LLC can do for your business.
1706 W. Texas Ave,
Midland, Texas 79701
Call us: (432) 520-3539